AI summary
The article discusses the challenges faced by video delivery platforms, particularly in managing short-form and long-form content. It highlights the differences in user behavior and technical requirements for each format, emphasizing the need for specialized Content Delivery Networks (CDNs) tailored for video. Key points include the importance of fast startup times for short-form videos and stable playback for long-form content, along with the necessity of edge security controls to combat unauthorized redistribution and abuse.
The core message is that effective video delivery requires a CDN designed specifically for video, which ensures reliable performance under load, predictable costs, and robust security measures. This is crucial for maintaining quality and protecting business models against unauthorized access and automated threats, which can significantly impact bandwidth costs and service stability.
Video delivery has some unique challenges. Short-form feeds have trained users to expect instant playback while they scroll. Long-form platforms have to sustain quality for minutes or hours without buffering. And some categories – especially platforms with high rates of unauthorized redistribution – face an additional constraint: hostile traffic (hotlinking, scraping, abuse) that can quietly become the biggest driver of bandwidth spend and outages.
This article explains how modern streaming platforms address these issues by leveraging specific types of CDNs. We’ll start with the basic delivery pipeline, then look at how short-form and long-form patterns differ, what CDN tuning really changes, and why some platforms need edge security controls as much as they need fast delivery.
Short-form vs long-form delivery – same pipeline, different priorities
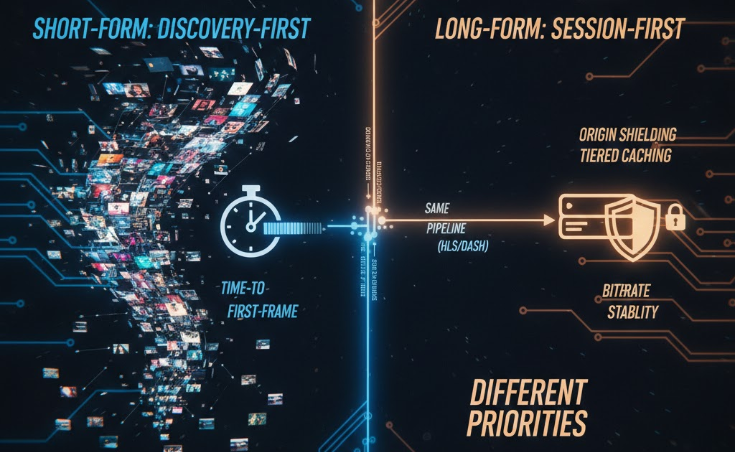
Nowadays, short-form and long-form videos rely on the same basic pipeline – HLS/DASH manifests and segments, an origin store, and a CDN close to users. The difference is what viewers do once they arrive, which changes what the platform needs to optimize for.
Short-form is discovery-first. Viewers start playback constantly and switch quickly. That makes “first frame fast” the product itself. Many short-form players also prefetch the next clip (or at least the first segments) so the feed feels instant. The upside is a smoother experience; the downside is increased bandwidth and greater caching complexity, because the platform is now delivering content users may never actually watch.
Long-form is session-first. Viewers tolerate a brief initial buffer if the rest of the experience is stable. Here, the real failure mode isn’t a slightly slower start – it’s rebuffering ten minutes in, or quality bouncing up and down because the player can’t hold a bitrate. Long-form delivery is therefore tuned around sustained throughput, predictable caching for popular titles, and protecting the origin from concurrency spikes through tiered caching and shielding.
- Primary metric: short-form prioritizes time-to-first-frame; long-form prioritizes rebuffer rate and bitrate stability.
- Traffic pattern: short-form creates many “starts and switches”; long-form creates fewer starts but long, steady sessions.
- CDN behavior: short-form leans harder on fast edge hits and prefetch; long-form leans harder on cache efficiency at scale and origin shielding during peaks.
Why CDN – the right kind of CDN – is needed for video platforms
When we say “CDN” in the context of video, we don’t mean a generic edge cache designed for web assets. We mean a CDN built and tuned for the realities of video: fast starts, stable playback under load, predictable costs at catalog scale, and the ability to enforce control on the media path.
A video-ready CDN is beneficial in three practical ways.
First, it improves startup and seek performance by ensuring requests are served from locations that can respond quickly and reliably. That can mean smarter routing decisions, better edge coverage, and caching behavior optimized for manifests and segments.
Second, it protects playback stability under concurrency. When thousands – or millions – of viewers hit the same content in a short window, the main risk is what happens when cache misses pile up, when capacity gets unevenly loaded, or when an origin suddenly becomes the bottleneck. A CDN that’s fit for video uses tiering/shielding and throughput-oriented delivery behavior to keep sessions stable through peaks instead of collapsing into buffering storms.
Third, it keeps costs predictable at a large library scale. Edge caches can’t handle large libraries, and naive “cache on first request” can turn the long tail into churn: cold assets consume storage and evict the hot ones that actually drive repeat delivery. The right CDN setup avoids paying origin egress for every repeat view of popular content, while also avoiding wasteful cache pollution from low-demand assets.
Lastly, for platforms operating in high-redistribution environments, there’s a fourth requirement that often becomes decisive: control at the edge. Hotlinking, scraping, and other forms of hostile automation can quietly become the biggest driver of bandwidth spend and outages. A video CDN can enforce access rules on the media endpoints themselves – so delivery is fast for real viewers and expensive (or impossible) for opportunistic reuse.
Security and abuse controls – when “delivery” becomes a control plane
Let’s talk about the last part some more. Unfortunately, at scale, streaming platforms don’t just serve viewers. They also serve scrapers, hotlinkers, credential stuffers, bots that download every rendition, and opportunistic mirrors that treat your media URLs like a free content API. If your delivery path can’t enforce rules, your CDN will still do its job – but not for your business.
Securing your content is now a core part of modern video delivery. It enables companies to maintain control over distribution while preserving legitimate traffic – because the hardest part of protection isn’t blocking obviously bad requests, it’s distinguishing abuse from real viewers when the technical signals overlap.
Hotlinking, in practical terms
Hotlinking is the simplest – and most economically damaging – form of unauthorized redistribution. A third-party site embeds your media in its own pages and streams it directly from your delivery infrastructure, using your bandwidth and your capacity, while monetizing the views for itself. You pay the bill; they get the traffic, the ads, and the upside.
Technically, it’s often just a <video>, <img>, or <iframe> pointing at your media URL. And the uncomfortable part is that, at the HTTP level, hotlinking can look a lot like legitimate access. The same browsers fetch the same manifests and segments. Headers can be spoofed. IPs can overlap. That’s why “one simple rule” rarely works in production.
Stop hotlinking and scraping with our Video CDN
A layered strategy: preserve real viewers, punish reuse
The security model that fits video delivery – the one we use Advanced Hosting – is always layered. You combine multiple mechanisms – each covering a different failure mode – so that legitimate playback stays smooth while unauthorized reuse becomes brittle.
- Source validation to reduce unauthorized embedding and basic hotlinking
- URL personalization and short-lived validity to limit link sharing and replay
- Geo controls to enforce where content can be viewed
- Transport and browser-side controls to reduce casual leakage paths
- Scraping and mass-access detection to identify automated behavior patterns
Why protection has to be adaptive
If you only rely on one signal – referrer headers, a user-agent string, an IP pattern – you will either block real users or let abuse through. The best systems evaluate multiple signals in context and make decisions probabilistically: not “is this header present,” but “does this request look like a real playback session.”
That’s particularly important in video, because bots now increasingly behave like users. They can load your site, obtain valid links, and then reuse them at scale.
CDN controls are necessary, but they’re not sufficient on their own. You also need bot detection and rate-awareness at the application layer (for example, monitoring unusual request volumes per IP/session) so attackers can’t simply harvest valid URLs and walk through the front door.
Secrets, signing, and safe rotation
Advanced protection mechanisms ultimately depend on a sensitive shared secret – used to sign URLs and/or encrypt them. Operationally, the critical feature here isn’t just signing – it’s rotation without downtime. Supporting two secrets simultaneously (a primary and an alternative) allows you to rotate credentials safely: validation succeeds if either secret matches, which prevents cutovers from becoming outages.
Making room for legitimate crawlers
Protection can also backfire in a quieter way: it can block indexing and reduce discovery if crawlers can’t access content that you do want searchable. The right approach is not “trust the User-Agent,” because headers are easy to spoof. Instead, if you offer a crawler bypass (e.g., for Googlebot), it should be based on verified authenticity – such as validating requests against Google’s published crawler IP ranges – so you preserve indexing without creating an easy bypass for attackers.
DDoS: what the CDN absorbs by design – and what needs escalation
A distributed video CDN architecture naturally raises the bar for low- to mid-scale attacks simply by spreading traffic across a large footprint. But “naturally resistant” isn’t the same as “immune.” If you’re a high-profile platform or you’ve seen targeted attacks, the right posture is layered again: baseline absorption plus additional mitigation options that can be enabled based on threat level, without breaking playback for real users.

Operators that need the most security
Now, let’s discuss who actually needs these controls the most, and who can treat them as just an optional hardening. In reality, most public video endpoints get probed. What changes is whether abuse stays a rounding error – or becomes a structural driver of cost, outages, and lost revenue.
Concrete signs you’re in the danger group:
- Your videos show up embedded on other sites with your URLs in the network trace.
- You see playback volume that doesn’t match on-site sessions, referrals, or ad impressions.
- A small set of assets generates disproportionate egress from “weird” referrers or no referrer at all.
- Traffic spikes originate from sources that don’t correlate with your own app releases, campaigns, or creators.
Here are some concrete types of platforms that often fall victims to attackers:
UGC and tube-style libraries with huge long tails
Large UGC libraries attract automated access the way open APIs do: they’re vast, continuously refreshed, and valuable to index, scrape, mirror, and re-upload. Even when the motivation isn’t direct redistribution, automation changes the shape of traffic in ways that hit cache efficiency and origin load.
Why it becomes a must-have here:
- Automation destroys the assumptions your delivery layer relies on. Real viewers cluster around a hot set; scrapers roam the long tail. That shift pushes more requests into “cold” territory, where delivery is less efficient and origin is hit more often.
- The long tail becomes an infrastructure tax. Random, low-repeat requests create more misses and more backend work per delivered minute than normal viewing does.
- Abuse scales quietly. It doesn’t arrive as one obvious attack. It grows as background noise until it’s a top contributor to origin egress and instability.
- Spikes become more dangerous. When a hot item trends, you’re already carrying an extra load from automation. Your “headroom” is smaller than your dashboards suggest.
For big libraries, security is as much about protecting the delivery model from distortion as it is about protecting the content.
Subscription and premium content platforms
If a stream has monetary value – subscriptions, PPV, creator paywalls – then leakage is a major risk. Some users will share access casually, and some actors will scale it systematically.
Why security becomes business-critical:
- Revenue leakage is direct and measurable. Every unauthorized viewer is a potential subscriber who never enters your funnel.
- Account sharing and session misuse create churn and support load. You see more “my stream stopped” and “someone used my account” complaints, which increases refunds and operational costs.
- Paid content becomes a target for industrialized reuse. The more valuable the content, the more likely links/sessions are to get redistributed in communities built around free access.
- Delivery cost rises without revenue rising. Your busiest assets are exactly the ones most likely to be reused outside intended access, so your highest-cost traffic can become your lowest-value traffic.
Here, security is less about “bad actors” in the abstract and more about protecting the unit economics of paid viewing.
Funtech and Adult platforms
Adult platforms often sit at the intersection of the hardest conditions: strong incentives for redistribution, deep catalogs, heavy sampling behavior, and a persistent background of automated access.
Here’s why protection is of the essence here:
- Unauthorized embedding and mirroring are routine. The category has a long history of sites monetizing other sites’ content, which means “reuse pressure” is constant.
- A lot of traffic is discovery-driven. High rates of starts, switches, previews, and short sessions amplify delivery costs – and make it easier for abuse to hide inside normal-looking playback behavior.
- Bandwidth spend can decouple from business growth. You can see delivery costs rise even when your own audience and monetization are flat, because consumption is happening outside your platform.
- Operational load is continuous. Takedowns, re-uploads, and reappearance on mirrors create a steady churn that turns weak control into ongoing cost.
Make large libraries economically deliverable
Enterprise and educational video
This category often doesn’t face the same redistribution incentives, but it still needs strong protection because the value is tied to controlled access and policy.
Why it matters here:
- The audience is defined. The platform’s value proposition depends on gating – employees, students, partners – not broad distribution.
- Policy constraints are part of the product. Region rules, time windows, and organizational access are not edge cases; they’re baseline requirements.
- Network reality is messy. VPNs, proxies, and corporate NAT make “simple” access assumptions unreliable; without robust enforcement, you end up with either leakage or broken playback for legitimate users.
- Auditability is often required. It’s not enough that content plays; access often needs to be attributable and explainable.
In enterprise/education, security is how you preserve the promise of controlled distribution without turning delivery into a fragile custom system.
The common thread across these categories is as follows: when unauthorized access or automation meaningfully changes who you’re serving, what your delivery layer is doing, and how your costs map to revenue, security stops being optional. It becomes one of the structural inputs into CDN design and operational maturity.
Summing up
The “video delivery problem” isn’t one problem. It’s a bundle of issues that compound each other as you scale. And in high-redistribution environments, abuse can quietly become the dominant source of both bandwidth spend and instability – because it looks like normal playback right up until the bill arrives.
That’s why the right CDN for video has to behave like production infrastructure built for video’s worst days:
First, stable delivery under load. Consistent first frame, consistent throughput, and fewer failure cascades when demand surges or routing conditions change. This is what keeps short-form experiences from feeling laggy and long-form sessions from degrading into quality oscillation and stalls when concurrency rises.
Second, control that protects the business model. If your category attracts hotlinking, scraping, mirroring, or systematic reuse, the delivery layer has to enforce distribution on the media path so your CDN doesn’t become a free backend for someone else’s site. It has to be able to prevent “cheap reuse at scale,” keep abusive traffic from polluting delivery capacity, and keep costs tied to real viewers and real monetization.
Taken together, this is what “video CDN” should mean: delivery that preserves playback quality while preventing non-viewer demand from redefining your economics.
If you want to know where your platform sits on this curve, reach out. We’ll review your current delivery flow and traffic patterns – and propose a Video CDN setup that improves playback, stabilizes peak behavior, and reduces the hidden bandwidth tax from abuse.